Important security update released for the Huddly L1 and S1 Windows IP camera driver
As part of our commitment to your security, we’ve got important news to share. A recent third-party security audit found a vulnerability in the IP camera driver for the Huddly L1 and S1 cameras. To address this issue, our engineering team immediately developed, tested, and verified a patch, which is now available in version 8.0.7 of the software. It started rolling out through Windows Update at the end of September, and most customers should already have this installed. It is also accessible on our website.
To make sure your devices are secure, please follow the instructions below as soon as you can.
Who is affected?
- If you have a Windows device where the Huddly L1 or S1 IP camera driver is installed.
- If you have ever installed the camera using the Network Adapter, even if you are currently using the USB Adapter.
How do you download the security patch?
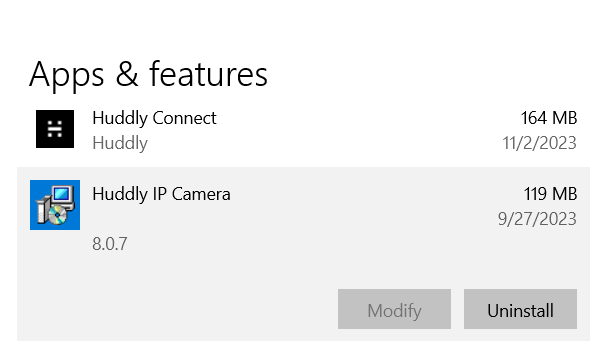
Most customers will most likely have received the update already as it was rolled out previously via automatic Windows Update (see dates below). Please verify if you already have version 8.0.7 or later by going to Apps & Features on your computer and searching for Huddly IP to see the currently installed driver version.
- If you don’t have the latest version installed, install it by either of the following steps:
- Update via the Windows Update on your computer.
- Download the new driver from our website here (see Step 2).
- Manually download the driver update from the Microsoft Update Catalog.
Patch release dates
The update was published on:
- huddly.com 21. September
- Windows Update 23. September (gradual rollout started on 23rd September and completed on 23rd October)
- Available on the Windows Update Catalog from 23. October
Date when the vulnerability is publicly disclosed on the CVE Database: 20.11.2023
Looking for more detailed information regarding the vulnerability?
For more information, please see the following documents:
Huddly Support is happy to assist if you have further questions. Contact us here.